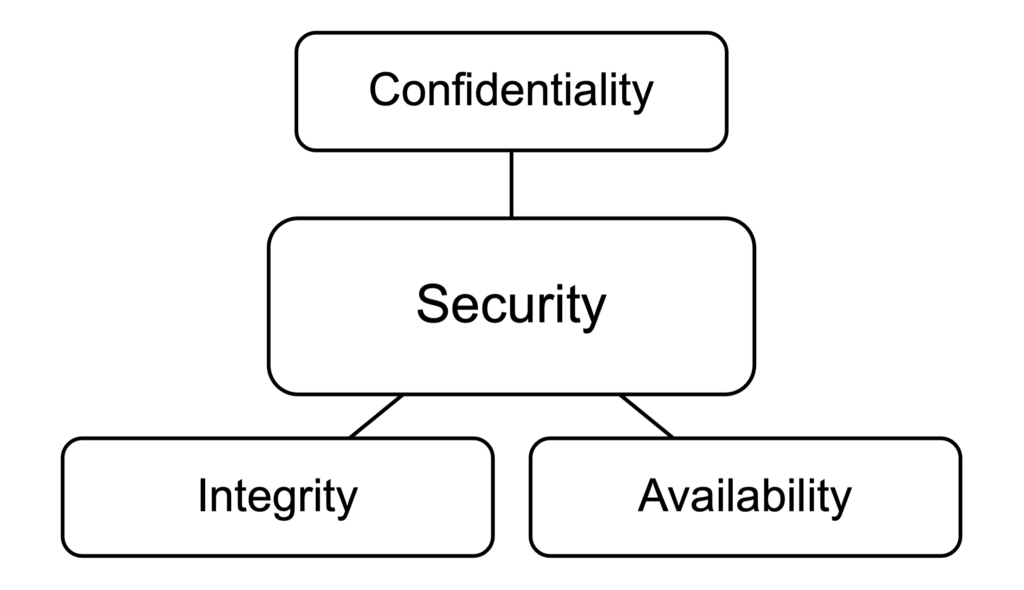
Network security would be very easy if no one ever needed to use computers or data. From a security point of view, it is unfortunate that people use networked computers. The reality is that we need networked computers and that data stored on them to do our work as educators. IT designers consider confidentiality, integrity, and availability when they design systems. Confidentiality means only authorized users access data. Integrity means the authorized user see all the data they need, and it is complete and accurate. Availability means they can get to the data from any location and at any time they need it. When designing IT systems, we seek to maximize security, but some things we do to make data available may threaten confidentiality. Further, some things we do to ensure integrity may make it less available, even to authorized users. Balancing all three is the challenge.